| Channel | Publish Date | Thumbnail & View Count | Download Video |
|---|---|---|---|
| | Publish Date not found | 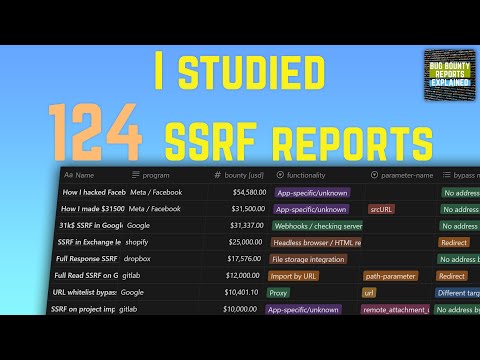 0 Views |
The blog post with case study methodology: https://bbre.dev/ssrfs
️ Sign up for the mailing list: https://bbre.dev/nl
Follow me on Twitter: https://bbre.dev/tw
I pulled 361 bug bounty reports from around the web to create a case study and see how people are making money with SSRFs. In this video, you'll learn which functions are most commonly vulnerable to Server-Side Request Forgery in these published reports, and also some of my opinions on which of them will become more popular in the coming years.
Videos mentioned:
12,000 Grafana SSRF in Gitlab: https://youtu.be/Uklsk1WZ2EU
31,337 hands-on exercises on blind SSRF labs on Google Cloud: https://youtu.be/ashSoc59z1Y
How I found the 1,500 SSRF in the Stripe bug bounty program: https://youtu.be/Ga9o–v-grA
An overlooked parameter leads to a critical SSRF in the Dropbox bug bounty program: https://youtu.be/sMk5ajkJO5o
Get 100 credits for Digital Ocean: https://bbre.dev/do
Time stamp:
00:00 Introduction
00:54 Import via URL
02:14 File uploads
04:39 Headless browser / HTML rendering
05:36 Check webhooks / server status
07:36 Proxying
09:16 Security mechanism / library error
11:43 File storage integration
13:23 Sentry integration
14:43 Host header
15:10 Email configuration
16:32 First request line
18:07 Get access to the full case studies and reports database
Please take the opportunity to connect with your friends and family and share this video with them if you find it useful.











