| Channel | Publish Date | Thumbnail & View Count | Download Video |
|---|---|---|---|
| | Publish Date not found |  0 Views |
Welcome to our channel where we dive into the world of cybersecurity with the latest updates, tips, and insights.
Whether you're a seasoned professional or just starting out, our videos are designed to keep you up to date and expand your cybersecurity knowledge.
In this video we cover important topics and provide valuable insights into the current cybersecurity landscape.
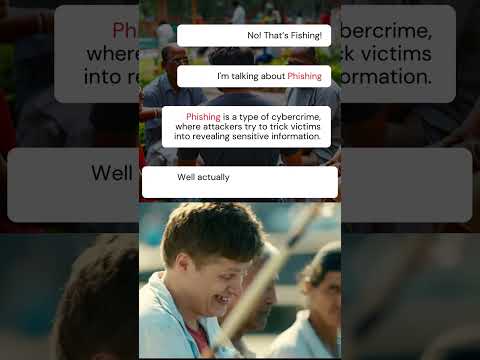
From spotting phishing attempts to securing your online accounts, these tips will help you stay safe in an increasingly digital world.
What you will learn:
How to create secure passwords and manage them effectively
How to recognize and avoid phishing attacks
Importance of secure connections and updates
SIEM Tools: Gain a deeper understanding of Security Information and Event Management (SIEM) tools, their importance in threat detection, and how to integrate them into your security infrastructure.
SOAR (Security Orchestration, Automation and Response): Learn how SOAR platforms automate security operations, improve responsiveness, and reduce time to incident resolution.
EDR (Endpoint Detection and Response): Discover EDR solutions and their role in identifying and containing threats at the endpoint level.
XDR (Extended Detection and Response): Discover the benefits of XDR for comprehensive threat detection and response across multiple security layers.
NDR (Network Detection and Response): Learn how NDR tools monitor network traffic to detect and respond to anomalies and potential threats.
OT Security (Operational Technology Security): Dive into the unique challenges and solutions for securing operational technology in industrial environments.
Cloud security:
Azure security: Tips and best practices for securing your Azure environment.
AWS Security: Learn how to protect your AWS infrastructure and data.
GCP Security: Key strategies to protect your Google Cloud Platform resources.
SOC Analyst Insights: Explore the role of a Security Operations Center (SOC) analyst, including daily tasks and the skills required for the job.
Security Analyst Jobs: Stay up to date with the latest cybersecurity job openings and career opportunities.
Top Security Companies and Products: Check out leading cybersecurity companies and their top products that can improve your security posture.
Networking Skills: Brush up on key networking concepts that are critical to understanding and mitigating security threats.
Cyber News: Get the latest updates on cyber threats, breaches, and trends impacting the cybersecurity landscape.
Vulnerabilities: Learn about the most critical vulnerabilities and how to protect yourself from them.
OSINT (Open Source Intelligence): Discover how OSINT can be used for threat intelligence and security investigations.
OWASP (Open Web Application Security Project): Understand the OWASP Top 10 and other key security frameworks for web application security.
Security Frameworks: Explore various security frameworks and standards that serve as guides to best practices in cybersecurity.
Endpoint Security: Learn about strategies and tools to protect endpoints from cyber threats.
Ticketing Tools: Insights into best practices for using ticketing systems to manage and resolve security incidents.
Monitoring, analysis and reporting: Techniques for effectively monitoring, analyzing and reporting security events.
Malware Analysis and Research: Learn malware analysis and research methods to understand and contain threats.
IoT Devices: Learn about the security challenges and solutions to protect Internet of Things (IoT) devices.
Stay up to date:
Follow us for daily cybersecurity news and updates.
For more detailed articles and resources, visit our website [insert link].
Connect with us on social media [insert social media links] to receive real-time updates.
Don’t forget to like, subscribe, and hit the notification bell to get the latest cybersecurity tips and news delivered straight to you!
#Cybersecurity #OnlineSecurity #CyberTips #TechNews #InternetSecurity #SIEM #SOAR #EDR #XDR #NDR #OTSecurity #CloudSecurity #AzureSecurity #AWSSecurity #GCPSecurity #SOCAnalyst #SecurityAnalyst #CyberNews #Vulnerabilities #OSINT #OWASP #SecurityFrameworks #EndpointSecurity #MalwareAnalysis #IoTSecurity #SIEM #SOAR #EDR #XDR #NDR #OTSecurity #CloudSecurity #AzureSecurity #AWSSecurity #GCPSecurity #SOCAnalyst #SecurityAnalyst #CyberNews #Vulnerabilities #OSINT #OWASP #SecurityFrameworks #EndpointSecurity #MalwareAnalysis #IoTSecurity #TechTips #InfoSec #DataProtection #ThreatDetection #CyberDefense #NetworkSecurity #IncidentResponse #CyberThreats #SecuritySolutions #Phishing #Fishing #PhishingAttacks #PhishingAwareness #PhishingPrevention #OnlineThreats #OnlineSecurity #EndpointSecurity #Virtualization #CybersecurityClips #CybersecurityShorts CybersecurityVideos
Please take the opportunity to connect with your friends and family and share this video with them if you find it useful.