Role-Based Access Control (RBAC) explained: How it works and when is it used
| Channel | Publish Date | Thumbnail & View Count | Download Video |
|---|---|---|---|
| | Publish Date not found | 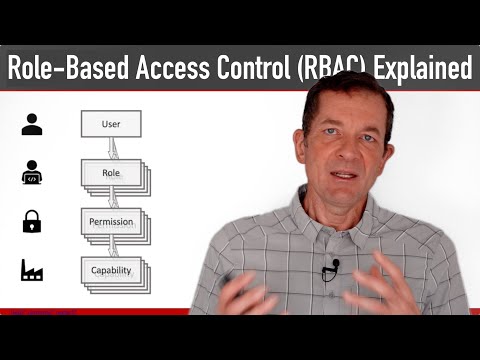 0 Views |
Role-based access control (RBAC) is a popular model for access control in large organizations. The reason for this is that it is highly scalable and can serve the access control needs of many large organizations well. While RBAC is not the only access control model available, it is very popular.
In this video, we'll walk through the main concepts of RBAC: capabilities, permissions, roles, and users. We'll also discuss the relationships between these concepts, such as the fact that users can play multiple roles.
Last but not least, we point out some alternatives such as Access Control Lists (ACL) and Attribute-Based Access Control (ABAC).
In this video, we'll walk through the main concepts of RBAC: capabilities, permissions, roles, and users. We'll also discuss the relationships between these concepts, such as the fact that users can play multiple roles.
Last but not least, we point out some alternatives such as Access Control Lists (ACL) and Attribute-Based Access Control (ABAC).
Slides online: https://dret.net/lectures/getting-apis-to-work-2021/rbac
0:00 Introduction to Role Based Access Control (RBAC)
0:41 RBAC Model: Ability
0:57 RBAC model: authorization
1:45 RBAC Model: Role
2:25 RBAC Model: User
3:38 RBAC Relationships: Users
3:47 RBAC Relationships: Role
4:18 RBAC Relationships: Permission
5:00 RBAC Relationships: Ability
5:49 Enterprise-level access control
Please take the opportunity to connect with your friends and family and share this video with them if you find it useful.











